Vulnerability Management Plan Template
Designers imagine you’re familiar with the fact that designers make people suppose that everybody needs a novel and expensive design which should be ordered from this designer specifically. vulnerability management plan template, however, are thought of to be sources of viruses, not cool in any respect and shameful. I suppose it is not fare enough to convince people do something they don’t actually need. That is why I decided to bust some myths about free template design.
A shift schedule template is a good way to simplify work rosters in massive companies that make use of folks across the clock. Known as a Shift Rota, it saves corporations time, not to mention expensive mistakes that handbook scheduling can result in. Most individuals resolve to abort handbook scheduling in favor of an expert template only after their group reaches a sure measurement and complexity. That is smart. There are solely so many vulnerability management plan template that can help with if there are only 3 folks obtainable. However, it is nonetheless important to grasp the fundamentals of creating a work schedule template with the intention to leverage the productiveness of your workers in the best possible approach.
Anyone could make a schedule chart in Excel. But, does the scheduling play to the strengths of the group? Does it guarantee sufficient rest for all workers? Does it consider private requests and particular person capabilities? Most importantly, does it make the most effective use of your accessible human sources? The more parameters, the extra advanced it’s to create a schedule that meets them.
Designing vulnerability management plan template is a reasonably easy chore. All it requires is basic information of the software used and a vivid imagination to seize the main points in an enchanting type. As an example, a seashore marriage ceremony would have an invite template depicting the solar and beach and frolic in the way it flows. Alternatively, a formal ceremony would demand a extra subtle movement in order to do justice to the theme as well. Customized wedding ceremony invitations literally go away the scope limitless when it comes to the imagination which can be used and the quantity of issues which could be included in a marriage invitation. The only factor to be adhered to is that the scale of the vulnerability management plan template and the articles therein are straightforward to print and appropriate to an excellent printer’s necessities. Thus, with some thought and effort, the apprehension of find out how to design vulnerability management plan templateL can be laid to relaxation.

nist security assessment plan template lovely 27 of

security assessment plan template lovely vulnerability
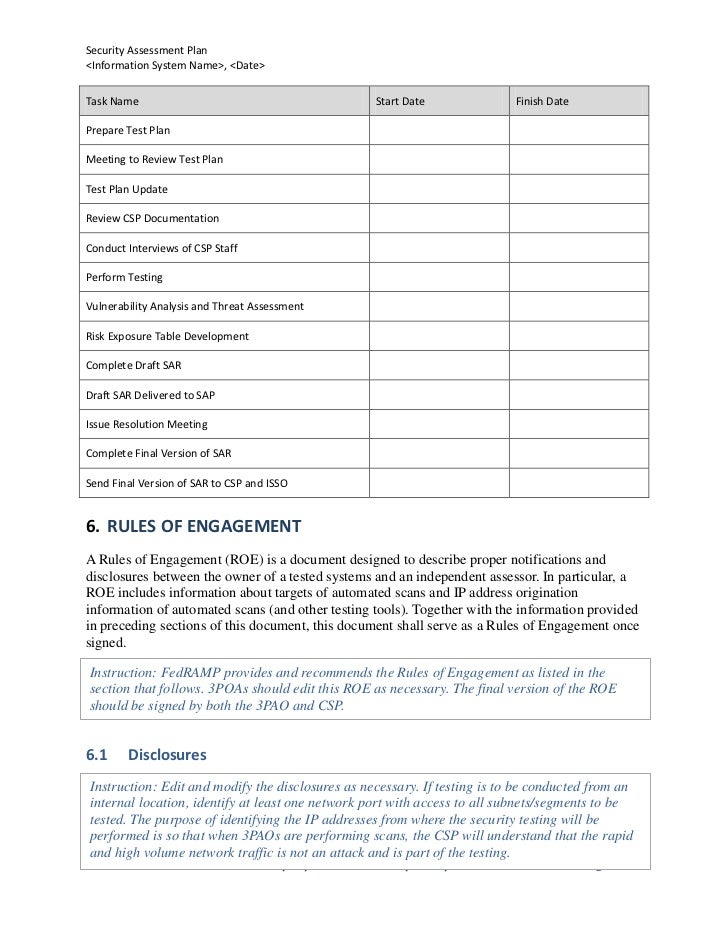
security assessment plan template
![]()
template free sample security vulnerability assessment

threat and vulnerability management nige the security guy
information risk management plan template in word and pdf

vulnerability management plan discovery scan report
![]()
template free sample security vulnerability assessment
0 Response to "Vulnerability Management Plan Template"
Posting Komentar